SSL and SSL Certificates Explained
Secure Sockets Layer (SSL) and Transport Layer security (TLS ) are protocols that provide secure communications over a computer network or link.
Security Provided
Keys and SSL Certificates
Obtaining a Digital Certificate
Example Usage
 Certificate Encodings and Files Extensions
Certificate Encodings and Files Extensions
Root CA Bundle and Hashed Certificates
mosquitto_pub --cafile /etc/ssl/certs/ca-certificates.crt
or
mosquitto_pub --capath /etc/ssl/certs/
Root Certificates, Intermediate Certificates and Certificate Chains and Bundles.
Video
Q- What is a trusted store?
Q- Can I add my own CA to my browser trusted store?
Q- What is a self signed certificate?
provide secure communications over a computer network or link.
They are commonly used in web browsing and email.
In this tutorial we will look:
- TLS and SSL
- Public and Private keys
- Why we need certificates and what they do
- How to get a digital certificate and understand the different common certificate types.
Security Provided
- No one has read your message
- No one has changed your message
- You are communicating with the intended person (server)
- How do you know that no one has read the message?
- How do you know that no one has changed the message?
- Encrypt it.– This makes the content unreadable so that to anyone viewing the message it is just gibberish.
- Sign it– This allows the recipient to be confident that it was you who sent the message, and that the message hasn’t been changed.
Keys and SSL Certificates
Obtaining a Digital Certificate
Example Usage
- Browser connects to server Using SSL (https)
- Server Responds with Server Certificate containing the public key of the web server.
- Browser verifies the certificate by checking the signature of the CA. To do this the CA certificateneeds to be in the browser’s trusted store( See later)
- Browser uses this Public Key to agree a session key with the server.
- Web Browser and server encrypt data over the connection using the session key.
- Domain Validated Certificates (DVC)
- Extended validation Certificates (EVC)
- mail.mydomain.com
- www.mydomain.com
- ftp.mydomain.com
- etc
- www.mydomain.com
- www.mydomain.org
- www.mydomain.net
- www.mydomain.co
- www.mydomain.co.uk
 Certificate Encodings and Files Extensions
Certificate Encodings and Files Extensions- Binary files
- ASCII (base64)files
- .DER
- .PEM (Privacy Enhanced Electron Mail)
- .CRT
- .CERT
Root CA Bundle and Hashed Certificates
mosquitto_pub --cafile /etc/ssl/certs/ca-certificates.crt
or
mosquitto_pub --capath /etc/ssl/certs/
Root Certificates, Intermediate Certificates and Certificate Chains and Bundles.
Video
- Here is my video that covers the points above.
- Here is a Microsoft video that I found that explains the above.
Q- What is a trusted store?
Q- Can I add my own CA to my browser trusted store?
Q- What is a self signed certificate?
TLS is based on SSL and was developed as a replacement in response to known vulnerabilities in SSLv3.
SSL is the term commonly used, and today usually refers to TLS.
SSL/TLS provides data encryption, data integrity and authentication.
This means that when using SSL/TLS you can be confident that
When sending a message between two parties you have two problems that you need to address.
The solutions to these problems are to:
Both of these processes require the use of keys.
These keys are simply numbers (128 bit being common) that are then combined with the message using a particular method, commonly known as an algorithm- e.g. RSA, to either encrypt or sign the message.
Almost all encryption methods in use today employ public and private keys.
These are considered much more secure than the old symmetrical key arrangement.
With a symmetrical key, a key is used to encrypt or sign the message, and the same key is used to decrypt the message.
This is the same as the keys (door, car keys) we deal with in everyday life.
The problem with this type of key arrangement is if you lose the key anyone who finds it can unlock your door.
With Public and Private keys, two keys are used that are mathematically related (they belong as a key pair), but are different.
This means a message encrypted with a public key cannot be decrypted with the same public key.
To decrypt the message you require the private key.
If this type of key arrangement were used with your car. Then you could lock the car, and leave the key in the lock as the same key cannot unlock the car
SSL/TLS use public and private key system for data encryption and data Integrity.
Public keys can be made available to anyone, hence the term public.
Because of this there is a question of trust, specifically:
How do you know that a particular public key belongs to the person/entity that it claims.
For example, you receive a key claiming to belong to your bank.
How do you know that it does belong to your bank?
The answer is to use a digital certificate.
A certificate serves the same purpose as a passport does in everyday life.
A passport established a link between a photo and a person, and that link has been verified by a trusted authority (passport office).
A digital certificate provides a link between a public key and an entity (business,domain name etc) that has been verified (signed) by a trusted third party ( A certificate authority)
A digital certificate provides a convenient way of distributing trusted public encryption keys.
You get a digital certificate from a recognized Certificate authority (CA). Just like you get a passport from a passport office.
In fact the procedure is very similar.
You fill out the appropriate forms add your public keys (they are just numbers) and send it/them to the certificate authority. (this is a certificate Request)
The certificate authority does some checks ( depends on authority), and sends you back the keys enclosed in a certificate.
The certificate is signed by the Issuing Certificate authority, and this it what guarantees the keys.
Now when someone wants your public keys, you send them the certificate, they verify the signature on the certificate, and if it verifies, then they can trust your keys.
 The important thing to note is that they start and end with the Begin Certificate and End Certificatelines.Certificates can be stored in their own file or together in a single file called a bundle.Although root certificates exist as single files they can also be combined into a bundle.On Debian based Linux systems these root certificates are stored in the /etc/ssl/certs folder along with a file called ca-certificates.crt.This file is a bundle of all the root certificates on the system .It is created by the system and can be updated if new certificates are added using the update-ca-certificates command. See hereThe ca-certifcates.crt file looks like thisThe certs folder also contains each individual certificate or a symbolic link to the certificate along with a hash.The hash files are created by the c_rehash command and are used when a directory is specified, and not a file.For example the mosquitto_pub tool can be run as:A certificate authority can create subordinate certificate authorities that are responsible for issuing certificates to clients.
The important thing to note is that they start and end with the Begin Certificate and End Certificatelines.Certificates can be stored in their own file or together in a single file called a bundle.Although root certificates exist as single files they can also be combined into a bundle.On Debian based Linux systems these root certificates are stored in the /etc/ssl/certs folder along with a file called ca-certificates.crt.This file is a bundle of all the root certificates on the system .It is created by the system and can be updated if new certificates are added using the update-ca-certificates command. See hereThe ca-certifcates.crt file looks like thisThe certs folder also contains each individual certificate or a symbolic link to the certificate along with a hash.The hash files are created by the c_rehash command and are used when a directory is specified, and not a file.For example the mosquitto_pub tool can be run as:A certificate authority can create subordinate certificate authorities that are responsible for issuing certificates to clients.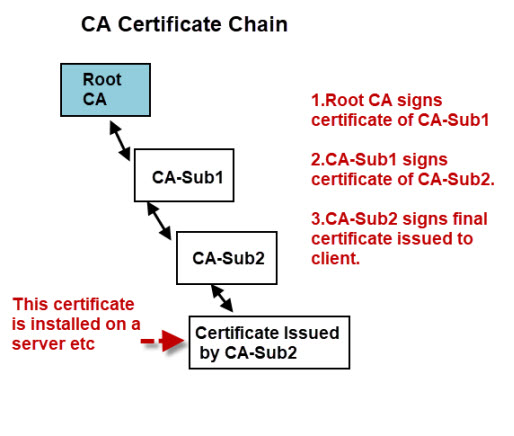
- For a client to verify the authenticity of the certificate it needs to be able to verify the signatures of all the CAs in the chain this means that the client needs access to the certificates of all of the CAs in the chain.The client may already have the root certificate installed, but probably not the certificates of the intermediate CAs.
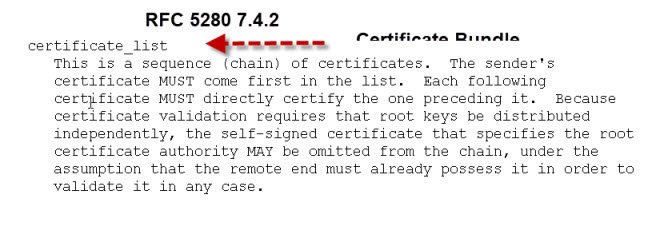
- Therefore certificates are often provided as art of a certificate bundle.This bundle would consist of all of the CA certificates in the chain in a single file, usually called CA-Bundle.crt.If your certificates are sent individually you can create your own bundle by following the steps here.A- It is a list of CA certificates that you trust. All web browsers come with a list of trusted CAs.A- Yes on Windows if you right click on the certificate you should see an install option
 A- A self signed certificate is a certificate signed by the same entity that the certificate verifies. It is like you approving your own passport application.
A- A self signed certificate is a certificate signed by the same entity that the certificate verifies. It is like you approving your own passport application.
Thank you for sharing such great information very useful to us.
ReplyDeleteDevOps Training
DevOps Online Training